Everyday, we’re being socially engineered – whether we realize it or not. Social engineering is a subliminal, psychological scheme that targets human weakness, making most of us vulnerable to these clever hacking techniques. From spam phishing emails to celebrity deep fakes, we see instances of social engineering all the time. Sometimes, it’s simply a funny Instagram reel or an annoying spam email that we just ignore but other times, social engineering can be really harmful. Social engineering – also called “human hacking” – is a method that cyber attackers use to take advantage of their victims. This might be to compromise a system, infect a network with malware, steal data or plainly fool users into believing something that isn’t true. The impacts vary in severity but unfortunately, it’s also something that can do a lot of damage.
How Does It Work?
Social engineering has a short cycle of steps that threat actors pursue to target their victims. They first prepare by identifying a target and doing reconnaissance. With that information, the attacker then selects a method they’ll use to target the individual. They’ll start by engaging the target, perhaps with an advertisement or video curated to them. This allows them to take control of the interaction and the user, by luring them in. Perhaps they’ll make the user click on a link with malware, or prompt the victim to provide certain data (like email or financial information) to an untrustworthy source. They might obtain information overtime by executing an attack and disrupting business and/or siphoning data. After that, their mission is complete: they accomplished their aim, got the information or data they sought after, and now can use it however they choose.
Social Engineering Isn’t Anything New: Trojan Horse Attack
The first record of social engineering dates back to ancient Greece, years and years ago. The catch? It had nothing to do with technology. You’re probably familiar with the Trojan Horse attack, where the Greeks deceived the Trojans to win their seemingly never-ending war.

After a 10-year siege, the Greeks built the wooden horse as per the orders of their leader, Odysseus, who came up with the idea. It was inscribed, said to be an, “offering to Athena,” hoping it would bless the Greek’s journey back home. The Greeks not only burned down their tents, but then pretended to sail away, to appear as if they had admitted defeat, only to return later, under the cover of the night. The horse was left behind and the Trojans figured it was theirs for the taking—a victory trophy, in their eyes. Then when the city of Troy was asleep, that’s when the men from the horse freed themselves, opening the gates for the rest of their army to assist with the infiltration of the city, thus revealing the true purpose of the horse. They destroyed the city of Troy from the inside out, putting flame to everything and finally putting an end to the war. The Greeks used the tactic of deceit to trick the Trojans. It has since become a classic learning lesson for many of us.
Similar to what happens with online cyber attacks, a threat actor attempts to overpower its victim by explicitly placing something out for them to take. The very thing they wanted – in this case, the horse – ended up doing them harm in the end.
Since Then…
The term social engineering was first used in 1894 by a Dutch industrialist named J.C. Van Marken. In 1911, Edward L. Earp wrote the book Social Engineer to encourage people to handle social interactions intelligently. Clearly, social engineering wasn’t just a term thrown around once technology became more advanced; it’s something that’s been around for over a hundred years. Ultimately, it boils down to all the ways in which humans can take advantage of others, for their own gain.
Deception Is an Art | Meet “The Condor”
Meet Kevin Mitnick: one of the most genius cybercriminals in the history of cybersecurity. He gained a lot of recognition – good and bad – for his immense familiarity with technology, and is most well known for his high-profile 1995 arrest, resulting in him having to serve time for his misdoings as a convicted hacker.
“I was an old-school hacker, doing it for intellectual curiosity.”
Interview with Wired Magazine, 2008
Back in the 1990s, he was one of the prime actors in popularizing the concept of social engineering, and after his release from prison, even became a published author on the topic, known for his work, “The Art of Deception.” We can attest to how incredibly insightful this book is, and we suggest anyone that relies on any form of technology, to read it at least once. Mitnick would go on to publish a total of four New York Times Best Sellers.




“It remains to be seen whether the man known as the Condor is an electronic criminal with the capacity to shred the Internet, as some of his angriest critics maintain, or, as his supporters say, the same pain-in-the-neck prankster who as a teen-ager turned off the phones of Hollywood stars for no other reason than to prove he could.”
The Los Angeles Times, 1995
Mitnick’s story is extensive and it was ripe with controversy. While many believed his crimes deserved punishment, some felt that the punishment given was excessive and not based on actual losses. Such perspectives inspired “Free Kevin” bumper stickers, as well as the hacking of Yahoo’s website, where a message was displayed on their homepage, demanding his release.
Kevin Mitnick hacked his first computer in 1979, just at the age of 16. He would be convicted of this crime in 1988, spending a year in prison. Shortly after his release, he would continue with his hacking ways. After two and half years as a fugitive on the run, his crimes would earn him a 46 month prison sentence, followed by 3 years of probation. In 1995, as per Kevin Mitnick’s Federal Indictment, he was charged with:
- Wire fraud (14 counts)
- possession of unauthorized access devices (8 counts)
- interception of wire or electronic communications
- unauthorized access to a federal computer
- causing damage to a computer
He stated that he mostly relied on social engineering exploitations, rather than just weaknesses in operating systems and software applications. This approach was unique because most hackers didn’t and don’t operate this way—and it made Mitnick one of the most notorious hackers in history. That really puts into perspective just how dangerous and sly these tactics can be. After all, deception is, in fact, an art.

Following Mitnick’s release from prison, he transformed his fascination with security into a positive and used his skills to help protect businesses and government agencies as a security consultant, teacher and public speaker. It was also exposed that he was diagnosed with Asperger’s syndrome; people with this condition are known to have IQs that are typical of geniuses, and they tend to become experts with very mechanical and/or technological things. It’s no surprise that he was called a “super-hacker.”
Common Social Engineering Tactics
There are a lot of ways to socially engineer. Threat actors can find their way to you in countless ways. Social engineering is far from a one size fits all, and can present in different forms, so it’s important to be mindful of how each type of social engineering tactic works.
#1: Phishing
The classic example of social engineering is phishing. It’s a huge cybersecurity threat to every industry and every business, and if not properly prepared for, can end up costing your company a pretty penny. Phishing is the practice of sending messages or emails that appear legitimate but are actually fake and dangerous. A common example of this is as follows: you get an email from your “boss” (or so you think) with an attached file. You click the link, without thinking, because you assume that it’s from your boss and must be important, right? Wrong. This message wasn’t actually from your boss but actually someone pretending to have a near identical email address as them. Now, the link you clicked is actually malware being deployed onto your computer, infecting your network.
Another type of phishing is known as “vishing” or “voice phishing.” In this case, attackers call their targets directly pretending to be an authority figure. They will usually ask for a payment or some sort of information, threatening the person on the other end. Phishers (and vishers) basically scam employees and individuals into doing something dangerous by using the art of deceit. They might trick people into revealing sensitive information, like credit card numbers or passwords, or into installing malware, ransomware, or some sort of virus onto their device. How is it social engineering? Well, in this case, hackers are taking advantage of our quick response time and tendency to not double check where messages might be coming from. We will then just click a link or share information without ever thinking, “Wait, do I know this guy?,” or, “How can I be sure that they are who they say they are?”
Recent Phishing Attacks
Phishing is a very real concern for many companies. Here are some fairly recent phishing attacks that made headlines:
- Feb 2022: NFT marketplace OpenSea lost nearly $2 million to phishing.
- March 2022: A number of clients at the bank Morgan Stanley had their accounts breached due to a vishing attack. The threat actor claimed to be a bank representative, seeking to create fake payments on their own. (This was not the fault of Morgan Stanley, but goes to show how real and harmful voice phishing can be).
- Nov 2022: Dropbox experienced a data breach caused by a phishing attack. The threat actor used a fake CircleCI login page to lure people in. They then copied a bunch of Github repositories and stole API credentials.
#2: Baiting
Baiting is similar to phishing in loads of ways. It follows the same steps, basically using illegitimate messages to deceive victims. The main difference is that baiting creates a promise of an item or a good to lure users in. They might offer “free” music, for example, as long as you click on the link and/or give them a few pieces of information. They can then use your actions against you in a baiting attack.
#3: Pharming
Though it seems similar and is usually paired alongside with it, pharming is not the same as phishing. Pharming is an internet scamming process where cyber criminals will redirect internet users to a “spoofed” domain. The link will look legitimate and imitate a real site, when it is in fact a fake, spoofed website. Then, the website might try to obtain a user’s personal information, including credit card number, social security, financial records, passwords, etc. A pharming attack can spread through malware in an email (known as malware-based pharming) or domain name system (DNS) poisoning. Pharming uses arguably more covert and advanced tactics with the goal of obtaining information from the target.
Phishing and pharming are paired together as the most popular forms of cybercrime:
#4: Malvertising
“Bad ads” are unfortunately becoming more common because they’re a tremendously surefire way to attract victims. Malvertising (malicious advertising) is a way of incorporating malware into digital advertisements. When there’s an ad pop-up on a website, it’s easy to just click on it without hesitation, especially if it’s the pair of shoes you’ve been dying to get or a discount for a new TV. Ads can come in a variety of shapes and sizes, typically in the form of pop-ups to side banners, and sadly, any of these advertisements could contain malware. Once a user clicks on a “bad ad,” it can deploy a virus onto a device, or prompt the user to click on another button to run malware.
Take a look at the Rhadamanthys Stealer campaign, a recent malvertising scam that was reported back in early 2023. In this scheme, a Google Ads campaign was spreading around malicious software called the Rhadamanthys Stealer. Rhadamanthys makes its way onto devices through spam phishing emails. These messages include a PDF attachment called “Statement.pdf” to lure users in. When clicked, a fake Adobe Acrobat update file appears, prompting the user to click “Download Update.” Upon clicking that, it downloads a malware executable, and boom, a bad ad can completely compromise your computer.
Malvertising has instances where it seems to be a little more thought out than other social engineering scams, as with the Rhadamanthys Stealer. This example might seem legit to a novice; after all, it takes you from a PDF to another link which appears real. It’s asking the user to do something seemingly important – updating a software – but is completely deceiving its target. That’s what makes malvertising (and other social engineering attacks) so dangerous: the way it easily grabs a user’s attention to act maliciously.

#5: Pretexting
A very common example of social engineering, which has made a huge appearance in the past year, is pretexting. Pretexting uses a fabricated story, known as a “pretext,” to gain a victim’s trust and trick them into sharing personal information. The threat actor starts by building credibility with the victim, usually by acting as a trusted individual (i.e., a coworker, service provider, staffer, romantic interest, etc.) Once they reel them in, they’ll plot a fake story, asking them to complete an action or share information of some kind. The use of pretexting is quite common in phishing attacks but differs in that, it’s far more targeted. For instance, a threat actor may prey on the elderly by pretending to be the victim’s child or grandchild in need of help. They’ll say, perhaps, that the grandchild was in an accident and needs money immediately. If you ever heard such news, your first thought probably wouldn’t be to question its legitimacy, and this is just one of the examples of the types of stories people will fabricate.
Scenarios that evoke panic are so cruel because they’re psychological in nature—but the scenario could be completely untrue. Pretexting preys on and seeks to leverage some of our very natural, human responses, such as:
- Social Trust: “A belief in the honesty, integrity and reliability of others”
- Our tendency to trust people and information
- Fight-or-flight response: A physiological reaction to a perceived threat
- Our ability to respond to emergencies on instinct, and without hesitation
- The Pain Pleasure Principle: our yearning desire to avoid pain and seek pleasure
By pretending to be a trustworthy individual or close to a relative, the attacker is able to build rapport with us almost instantaneously, resulting in lowered defenses, and thus, potentially allowing them to gain confidential information, only to then use it against us. Learn to make a habit out of double-checking that people are who they say they are. If you can’t confirm, then don’t act.
#6: Tailgating
Quite different from online social engineering tactics, tailgating is an in-person social engineering tactic, and.. it’s kind of crazy. Similar to when another driver follows right behind you on the road, attackers might do the same to enter a building and gain access to restricted areas. They might disguise themselves as an employee, postman, delivery driver, or someone else who would typically be granted easy access to the office but in reality, they’re just trying to get access to information to plan their next attack. This method isn’t necessarily the easiest for hackers to accomplish, as they need to physically be there. It may not be as common but it’s still a possibility and something that businesses should be on the lookout for – just in case.
#7: CEO Fraud (BEC)
CEO fraud is an example of BEC (business email compromise), which is a sophisticated scam in which cyber criminals target individuals/businesses for financial gain. The attacker utilizes social engineering by usually impersonating a high-level executive to take advantage of another employee. This is sort of like a phishing scam but takes a lot more preparation and understanding on the attacker’s side. They must familiarize themselves with the structure and purpose of the organization they’re targeting. They can then gather key individuals to target and impersonate, and then either gain control of the executive’s email via hacking or by creating a near-identical email address. For example, the attacker might go through an executive’s position to email an employee and request a transfer of funds.
#8: Dumpster Diving
As the old cliche goes, “One man’s trash is another man’s treasure.” Dumpster diving in the IT world is when an individual digs through the trash to retrieve information, so that users can get unauthorized access to a computer network. Even if the information in these documents is seemingly innocent, like a phone list or calendar, it can still be cleverly used against you. Diving for computer hardware can be a gold mine for hackers, especially because so many people don’t wipe and discard their old devices properly. Dumpster divers can take advantage of the information stored on old computer hardware, putting you/your business in a vulnerable position.

Where Is Social Engineering Going to Take Us?
Social engineering has been used to a great extent, and with the evolution and growing trend of artificial intelligence (AI), many wonder where it’ll take us next. Technology has taken the age-old concept of social engineering to a whole new level, as seen in the past 30 years.
People Might Not Be Who You Think They Are
Perhaps you’ve heard the term “catfish” thrown around a lot. People can completely pretend to be another individual online just by using a different profile photo, name, age and other falsified information. Maybe you start chatting with a new user on Facebook or Twitter. While you might think you’re speaking to a 30-year old girl with brown hair, it could actually be a cyber criminal from another country, and unfortunately, these hackers behind the screen are literally using social engineering to deceive you. What do they want? Money, passwords, personal information, just about anything you’re willing to fork over.
Now, it’s easy for them because they gained your trust as someone you think you know, when in reality, you don’t know them at all. These days, “people” can even be AI generated – so you can have an AI profile photo with an AI chatbot behind the scenes speaking to users, and you may never know the difference. Technology is literally replacing people in this case, and they might be able to gain information from users by implementing social engineering tactics.
Deep fakes are one of the many dangers of AI. These videos often surface around the internet, where people use AI to dub voices and mannerisms, to create fake videos of celebrities, politicians, and other public figures. These videos are often humiliating in nature and harmful to one’s reputation, and that’s entirely the point. Deep fakes can seem so real, that we often believe it’s the person we think, even when it’s.. not. Deep fakes are yet another example of how AI has impacted social engineering and how people can be deceived by artificial intelligence.
Attacks Can Be Specifically Catered To You
Many cyberattacks tend to take a general, blanketed approach. Like a fishing net thrown into the sea, one tactic can be used to lure and exploit multiple victims. Social engineering, on the other hand, can be used to target specific individuals and businesses. Social media presence and internet usage has made this even easier. Hackers know how much we love to follow other people’s Instagram accounts and do online shopping. They can easily gather information through a social media post, even something as simple as your cat’s name, and use it against you. How could they use information like that? Well, they can then create a phishing email or phone scam to lure you in. The thing is: they know something about you that you wouldn’t want them to know. Any information is too much information in a sea full of sharks.
The Numbers Are Only Going Up
Risks are getting riskier, costs are getting costlier. The amount of social engineering scams is only going to increase in the future, and the ways it impacts businesses will only get worse. Attacks involving phishing, pharming, baiting, and other social engineering scams involve a lot of time and money to escape the problem at hand. Verizon’s 2023 Data Breach Investigations Report details just how much of a threat social engineering has been, and is becoming. What should your business know? 74% of data breaches in the past year involved human usage – that includes social engineering. 50% of social engineering attacks involved pretexting, which was just about doubled from the previous year’s total. Other common threats were phishing and use of stolen credit cards. The median amount of money stolen through social engineering attacks has increased over the past several years, now at $50,000. The graphs below show a breakdown of common social engineering attacks and the increase in pretexting incidents over time for the last 5+ years.
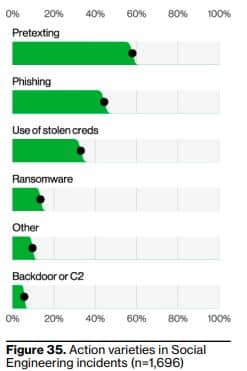
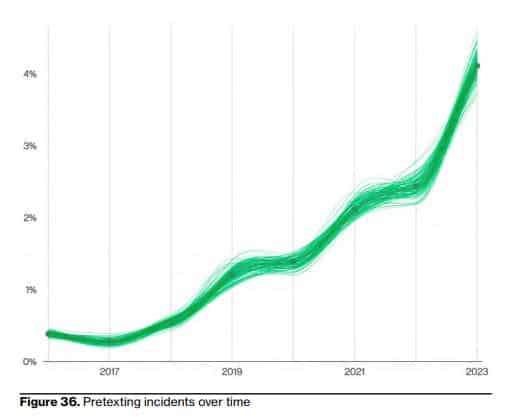
Source: Verizon’s 2023 Data Breach Investigations Report (DBIR)
Avoid Falling for Social Engineering 101
How can you avoid falling victim to social engineering scams? We’re all human, after all, so it’s unfortunately easy for others to take advantage of what they know many of us would fall for. Here are ways to best prevent social engineering:
- Cybersecurity Awareness Training
- No one should be exempt from this, including owners, executives, managers, shareholders, etc
- Beware of senders and callers,
- Get into the habit of double checking, it’ll become 2nd nature in no time and you’ll be more secure because of it
- Don’t click suspicious ads/links
- Don’t share names, locations, or private information of any kind online and on social media sites
- Make smart choices and don’t act on impulse
- Think things through before acting on them
- Always fact check—do your own reconnaissance
- For instance, if someone says they’re from a certain company and they’re asking something of you, ask for them to first verify their identity by contacting you from their business email address first, to confirm that it is in fact them





0 Comments