According to data compiled by the FBI, business email compromise (BEC) is one of the most damaging cyber crimes. All businesses rely on email to communicate, making almost any employee or client vulnerable to some level of compromise, which could be devastating financially, personally, or professionally. In 2022, the FBI’s Internet Crime Complaint Center received over 20,000 reports of BEC, with total adjusted losses of more than $2.7B USD. These threats can no doubt be very costly, which is why keeping your company safe from BEC is crucial. There are many ways your business can be at risk when it comes to business email compromise. Let’s take a look at what BEC is and how business email compromise works to better understand and protect our businesses.
What Exactly Is BEC?
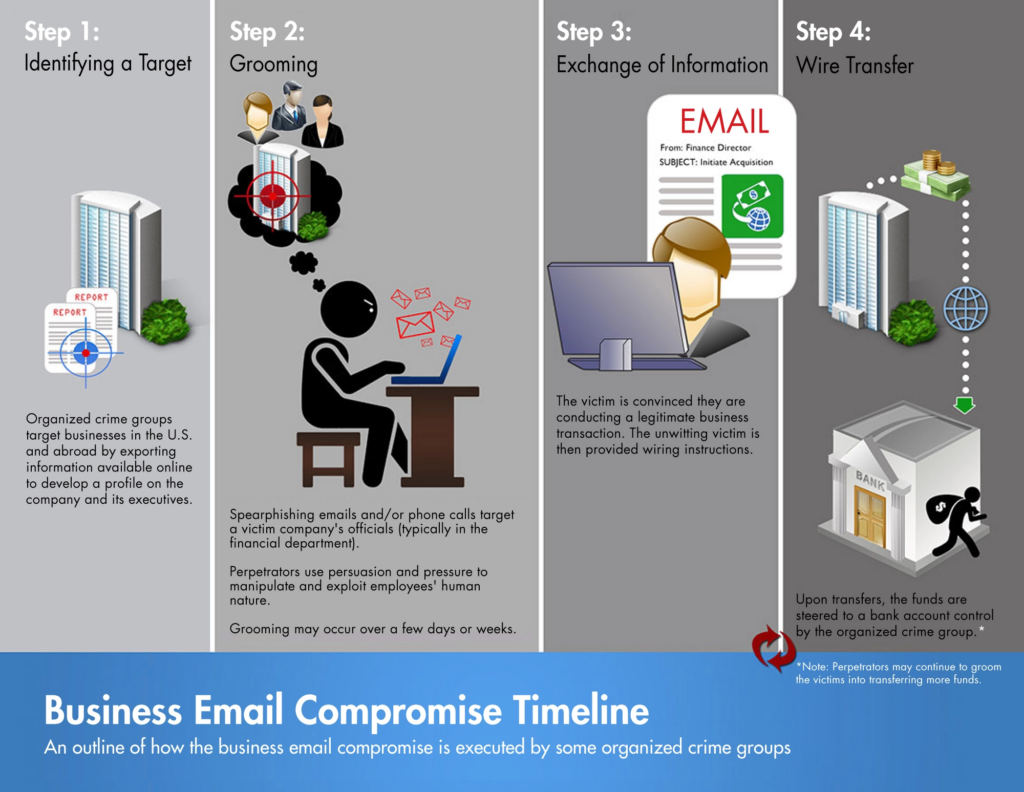
Business email compromise (BEC) is a scam in which cyber hackers will try to get targeted individuals and/or businesses to perform a transfer of funds. Criminals utilize social engineering to send email messages that look legitimate but are actually deceptive and typically quite dangerous. They also use, “computer intrusion techniques,” to transfer funds.
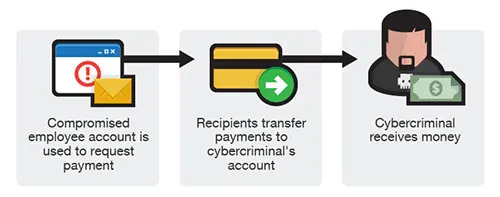
Source: Trend Micro
How Business Email Compromise Works
BEC uses more sophisticated social engineering techniques than a typical phishing email. Generally, phishing emails are easier to spot than BEC messages because they are generic and often sent out to millions of people (spam). They might contain your name in the intro, but otherwise, contain pretty basic messages that do not specifically target you or your company. With BEC, on the other hand, hackers will try harder to cater these messages to their victims, making them even more challenging to detect. They appear more genuine to the target, which is exactly what social engineering tries to do: trick you!
BEC is not specific to any industry (as previously assumed), so every company should be aware of the risks and on the lookout for any emails that look off in some way. Hackers will try to target the emails of any type or size of business/organization, especially those who have suppliers overseas, and often conduct wire transfers. Historically, BEC schemes often involved vendor emails, tax documents like W-2s, and targeted the real estate and financial sector.
Cyber criminals have recently been utilizing cryptocurrency to target victims (which will be covered more later). They might target custodial accounts held at banks and financial institutions, or simply ask victims to directly send funds to crypto platforms. In 2022, the IC3 saw a slight increase in the number of attacks on investment banking accounts rather than traditional financial accounts.
Types of BEC Scams
According to the FBI, there are five types of BEC scams. These are all relatively common. It’s important for all employees to be on the lookout for and understand how these business email compromise scams work.
Attorney Impersonation
In this case, a hacker will pretend to be a lawyer or representative of a law firm. They’ll claim to be handling time-sensitive, confidential matters, pressuring employees to wire or transfer money to a fraudulent individual.
Data Theft
Contrary to some of the other attacks, data theft does not involve the immediate wiring or transferring of funds. Instead, a hacker might specifically target an employee who has a lot of personal information, like someone in HR. They’ll then exploit this individual to steal the data of other employees, the company itself, or its clients.
Email Account Compromise (EAC)
EAC, also known as email account compromise, is a very common type of business email compromise. A cyber attacker will hack an employee’s email account and use it to make requests for different payments. What’s the difference between BEC and EAC? In the case of BEC, an attacker is pretending to be you, without having direct access to your email account. With EAC, they’re acting as you via your actual email address (not one that closely resembles it).
Bogus Invoice Scam
Referred to as the “Supplier Swindle” or “Bogus Invoice Scam,” this attack involves companies that have relationships with an external supplier. An email will contain a message asking for financial information, a payment/invoice, etc., from a fraudulent sender. When unaware that this is a scam, the recipient might deliver money to the fake sender, without even realizing it.
CEO Fraud
Attackers try to pretend they are some high-level employee, like a CEO, CTO, or CFO, and send a message to another employee. They might include information about a “time-sensitive” or “confidential” matter. A user who believes this is actually a high-leveled employee may end up wiring money to a fraudulent sender.
Business Email Compromise Working with Cryptocurrency
The FBI reported an increase in the use of cryptocurrency with business email compromise. Crypto has, in general, come under a lot of scrutiny since the downfall of FTX. Cryptocurrency is a type of digital currency that uses cryptography and coding in order to secure financial transactions. Hackers love to use cryptocurrency because most assume it’s untraceable but it turns out, that’s not entirely the case. The FBI detected two types of financial transfers with BEC: direct transfer and second hop transfer. Direct transfer of cryptocurrency is similar to traditional transfer tactics seen with BEC in the past. Second hop, on the other hand, uses victimization tactics like extortion. They attack individuals who might have provided copies of personal or financial information in the past, including driver’s licenses, passports, credit cards, addresses, etc. That information is then used to open crypto accounts under their names.
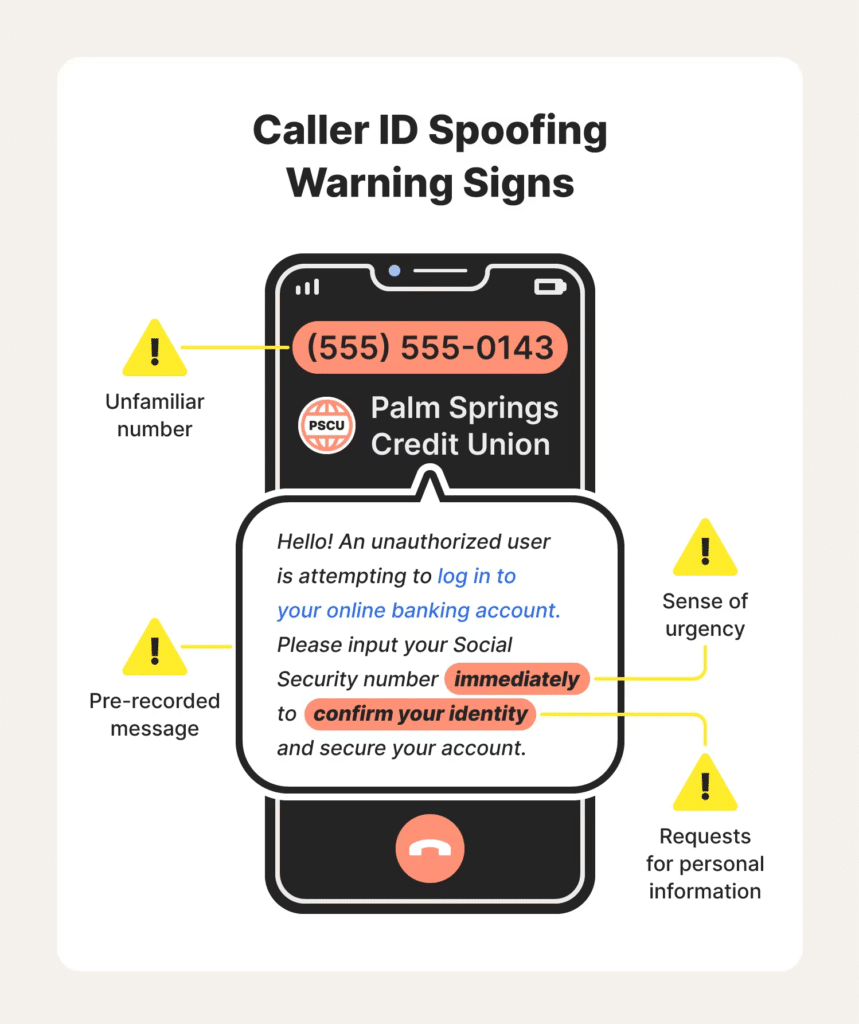
Increased use of Spoofed Phone Numbers
In 2022, IC3 saw more advanced tactics that cyber criminals used to trick victims into believing they were actually legitimate—one example is the use of spoofed phone numbers. The FTC defines spoofing as, “when a caller deliberately falsifies the information transmitted to your caller ID display to disguise their identity.” Spoofers can fake the name that shows up on Caller ID, as well as the actual number itself. All spoofing, which is really a broad term, involves a cybercriminal disguised as a trusted entity or device, intent on getting you to perform some action that’s usually favorable to the hacker but unfavorable to you. Spoofing can be done through email, text, phone calls, falsified websites and more. The use of spoofed numbers emphasizes just how important two-factor or multi-factor authentication is.

Who’s at Risk for BEC?
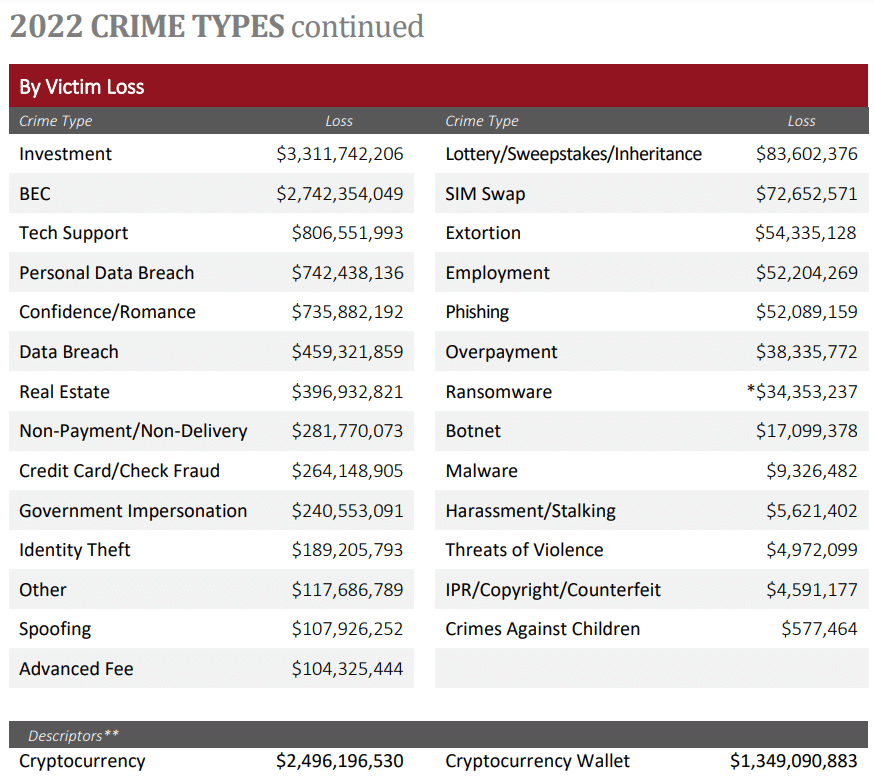
Every business can be threatened by business email compromise, so no one should take this issue lightly. The FBI’s 2022 Internet Crime Report details the statistics related to BEC in New York during the year 2022. The report states that there were 21,832 victims of business email compromise with a total loss of $2,742,354,049 in the year 2022.
Investment and BEC were the only two cyberthreats that totaled in billion dollar losses, with others being in the millions. Looking at the statistics from the 2021 IC3 report, there was a dramatic increase in the number of victims and amount of money lost from BEC. In 2021, the report shows that there were 1,373 victims of BEC/EAC, garnering a total loss of $252,406,676. Data also indicates that older individuals (60+) are more at risk for a lot of the crimes listed in the 2021 and 2022 IC3 reports, which likely correlates with cyber-related threats like BEC. The amount of victims increases by age group.
An FBI alert from mid-May of 2022 details the statistics of domestic and international BEC incidents. From June 2016 to December 2021, there were $43,312,749,946 domestic and international losses, and 241,206 domestic and international attacks.
Avoiding BEC
Now that we have a better understanding of how business email compromise works, we can use safe cyber practices to prevent it. Here are some tips to avoid BEC in your company.
Business-Grade Antivirus Is Your Best Friend
At Computero, we trust Trend Micro XDR for the best antivirus protection. Trend Micro goes above and beyond and will even alert you if they see a “risky” or “spam-like” email in your email account. For example, a spam email from a phishy sender might be marked by Trend Micro, signaling you to be careful when opening the email, or simply suggesting that you not open it at all. You can even have an email filter in Gmail called “Risky by Trend Micro.”

Multi-Factor Authentication
Protect any email accounts or financial information with two-step verification. Always use strong (long and complex) passwords and make sure there are multiple layers of verification so that individuals will not get unauthorized access to your accounts.
Monitor Financial Accounts
It’s generally good advice to keep an eye on all financial activity on a routine basis. Alert officials, as well as your bank, if you see something suspicious. This could be an example of BEC or other types of fraudulent cyber crime, especially if the sum of money being transferred is high.
Cybersecurity Awareness Training
Educating employees about threats like BEC and EAC will help to alleviate some of the likelihood of such an attack. When employees better understand just how harmful a simple click of a button can be, they’ll be more cautious when looking through business and personal email, as well as when surfing the web. Cybersecurity awareness training is essential to protect businesses from any sort of cyber attack, not just BEC.
Strengthen Business Security Requirements
Administrators should require that all individuals use two-step verification and strong passwords. Turning this from a mere suggestion to a policy is your best bet. This’ll tighten the default security requirements for the entire organization.
Authenticate Emails with Domain Authentication
Another solid layer of verification is known as domain authentication. Some good authenticating senders include Sender Policy Framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-based Message Authentication, Reporting, and Conformance (DMARC).
Have a Secure Payment Platform
Think about shifting away from emailed invoices to a system that’s created specifically to authenticate payments.
Subscribe to the FBI’s IC3 Updates
The FBI’s Internet Crime Complaint Center posts frequent PSAs regarding BEC and other schemes to look out for. It’s wise to stay up-to-date on fraudulent trends, like those targeting real estate, W-2s, and prepaid cards, for instance. Visit www.ic3.gov to learn about these important alerts.
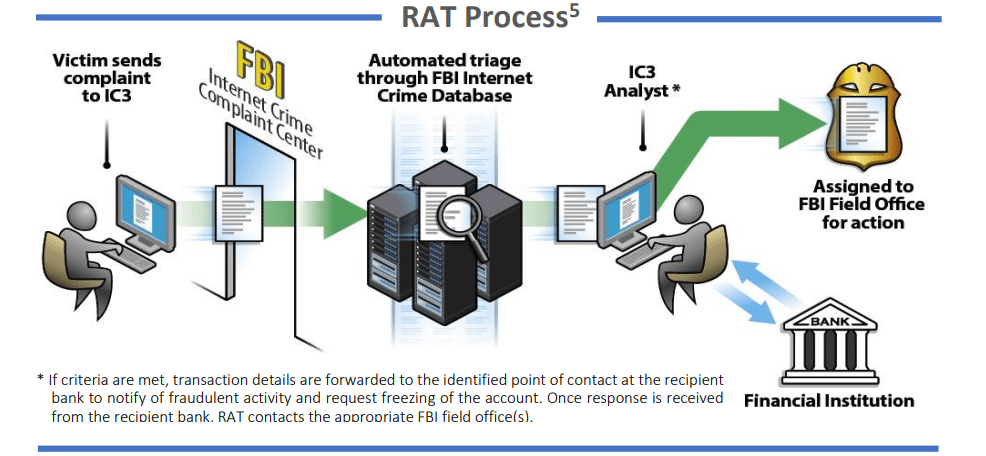
Report Any Cyber Crime to FBI’s IC3 Division
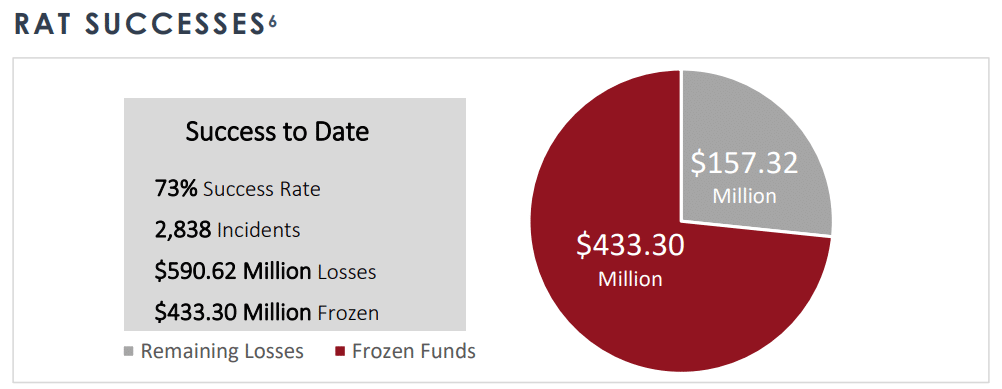
Most importantly, if your business has been targeted and experiences any sort of BEC, you can report it by filing a BEC complaint on the FBI’s IC3 website. You can also file a complaint about other instances of cyber crime, including ransomware, elder fraud and more. It’s pretty impressive the amount of money the IC3 Recovery Asset Team (RAT) has managed to freeze and return to both individuals and businesses that have been victims of cyber crime.
The IC3 provides these instructions regarding what information you should be ready to provide:
- Date of the incident
- Summary of the incident
- Victim Name
- Victim location (City, State)
- Victim bank name
- Victim bank account number
- Beneficiary name
- Beneficiary account number
- Beneficiary bank location
- Intermediary bank name
- SWIFT/IBAN number
- Date of transaction
- Amount of transaction
- Copies of emails, including header information
- Full screenshots are best if possible
- Check out the GoFullPage extension for Chrome
- Or simply, save the email as a pdf
- To do so, select the Print option and then hit the dropdown next to the Printer and select “Save as PDF”
- Full screenshots are best if possible
Protect your Business from BEC
The best way to protect your employees from business email compromise is with proper education and training. Employees should understand what it is and how business email compromise works so they can make smart decisions online. Cybersecurity awareness training is critical for any business, from small businesses and startups to Fortune 500 companies. The unfortunate reality is that unless you’re trained to be hyper aware of online safety, any company can be the victim of a cyber attack. A good cybersecurity awareness training program should be seen as an investment and will teach employees about compliance, as well as implementation of good cyber practices.
If your business encounters BEC, follow these instructions provided by the FBI’s IC3 division:
- On international transactions, contact your financial institution to issue a “SWIFT recall.”
- For domestic transfers, request your financial institution send a “hold harmless letter” to the beneficiary bank.





0 Comments