Does a Passcode (PIN) Really Protect your Phone in Public?
Everyone puts a passcode (PIN) on their cell phone to keep their information safe (well, we hope 😅) but is it really all that secure? The Wall Street Journal recently reported about an iPhone crime wave that NYC detectives have been monitoring closely, and their investigation highlights just how easy it is for thieves to gain access to your entire life within seconds. The end result is far more disturbing than having to just shop for a new phone: iPhone identity theft is very real. Victims saw thousands of dollars vanish from their accounts, to name just one of the by-products of the meticulously crafted identity theft scheme. Some victims were even drugged. All because of inadequate protection and a stolen iPhone.
How Apple iPhones Make Identity Theft Absurdly Easy
All a thief has to do is witness you type in your passcode and it could be over. Thieves simply look over your shoulder to see the digits you type in to unlock your iPhone, memorize or record the passcode, and seconds later, rip the phone from your hands. Now they can access everything on your phone – and surely, there’s a lot of confidential information that you probably keep in the palm of your hands.

It’s a bizarre reality but it really is that easy for criminals to gain access to all of your personal information. As long as they see you type in your passcode – which is something many of us do regularly, without conscious thought – they have all they need to change your life and steal your identity. To make matters worse, these thieves can have zero tech skills and still manage to do a lot of damage within just moments. One victim reported having her Apple ID password changed within just 3 minutes. That’s some criminal dedication.
If you put your phone in your back pocket or ever leave it out in the open, all a thief has to do is take it. This concern isn’t entirely new; it’s synonymous with entering your pin at the ATM or when purchasing something at the market. Even then, savvy shoppers are still vulnerable because criminals can be surprisingly clever. Despite hiding the pin you input into a credit card processor, you can still be exploited. How so? Thermal imaging cameras. Smartphones present a more complex challenge because their convenience is irresistible. Unfortunately, that convenience can cost us; if you’re targeted and your phone is stolen, your life could become quite dark very quickly. Are you ready to go back to flip phones yet?
2023: A String of NYC iPhone Thefts Reported
In a video interview with The Wall Street Journal, a woman described her personal experience with an iPhone theft outside of a bar in New York. Someone stole her phone, and as a result, immediately had control of her accounts. She stated that within less than 24 hours, she “noticed there were thousands of dollars being taken out of [her] bank account.” This isn’t the only instance of an iPhone theft in the US. In fact, just back in December 2022, an investigation into a Minneapolis theft ring led by Alfonzo Stuckey, resulted in 12 people charged with racketeering, who were found to have collectively stolen approximately $300,000 from 40+ victims.
What Do Thieves Do With Your Phone?
So a thief maybe sees your passcode and works to the next to step to get your iPhone. But what do they do with it that actually makes this identity theft? Here are the simple steps these thieves are taking that have lead to countless cases of iPhone identity theft. All due to Apple’s seemingly convenient — but very unsafe — chain of events.
How They Target Their Victims
In most cases, once thieves acquire the victim’s passcode, they swiftly take the user’s iPhone. Many thieves target bar goers because it’s relatively easy for them to intentionally distract even slightly intoxicated victims, making it easier to grab their phone in a flash. Bar goers are often distracted by conversations, mingling, and the general crowded atmosphere. It makes them a good target for thieves to quickly grab their cell phones, which they might leave out in the open on a table or hold casually in their hands, not even considering that the basic act of using their phone in public could make them a target.
First Thing’s First…
Once they get the phone, the thief’s first step is usually to change the user’s Apple ID passcode, locking the owner from accessing their own account. For Apple users, their Apple ID is the gateway to everything within the Apple ecosystem, containing a user’s personal data and settings. Many users have their Apple ID connected to other devices as well, like their MacBook or iPad. When thieves change the passcode, this jeopardizes any and all connected Apple devices.
Thieves will then turn off Find my iPhone, a feature that Apple offers to allow users to know the location of their Apple devices (including phones, airpods, laptops, iPads, and so on). When iPhone users lose track of their phones, they might use a friend’s device or their own personal Apple device to log into Find my iPhone and track it. But thieves can easily disable this feature by just hitting a toggle, suddenly making it nearly impossible to find your phone. One victim interviewed by WSJ says that she immediately tried to log into Find my iPhone on her friend’s phone once she realized her iPhone went missing. However, in the short time that passed, the thief already changed her Apple ID password so she couldn’t access Find my iPhone.
Get Rid of the Recovery Key
Unfortunately, it’s quite easy for thieves to access and change a victim’s Apple ID password through the iPhone’s “Settings” app. All the thieves need to know is the iPhone’s passcode—not even the original Apple ID password, which is already stored on the device. After changing the Apple ID password, thieves will go through the iPhone’s settings again to sign out of all trusted devices and remove what Apple calls the “Trusted Phone Number,” which is usually your cell phone number. (Why can’t they just call it what it is? A recovery phone number used for 2FA.) The final nail in the coffin? Thieves will then enable the “Recovery Key” option, locking you out of just about everything. This shouldn’t be confused with a security or hardware key; they’re not the same.
What is a Recovery Key?
The recovery key option makes it impossible for victims to regain access to their Apple ID account. The phone is now in the hands of a thief. While the recovery key is meant to “improve the security of your account,” in this case, it severely jeopardizes it.
Two factor authentication (2FA) security keys differ from Apple’s recovery key (they actually offer a lot of benefits). These are usually physical keys that the owner has. Without them, unauthorized users cannot access any accounts, even if they know the password. With Apple’s recovery key and its entire system being cloud-based, there is a huge risk involved with saving everything onto one single account. If a thief knew the login for let’s say your email account, but that required a security key to get in, it would be much more difficult to access your account. It’s incredibly unlikely that a thief would have both your password and security key. In the case of the iPhones, however, a recovery key is entirely different. If a thief enables this feature, it’s because they’re using it against you to further safeguard their recent possession of your device.
Now What? The Gateway to iPhone Identity Theft
Well, the thief has access to just about everything. They might choose to do some damage and literally steal your identity, all through iPhone theft. They might go through bank statements, photos, accounts, and much more, which is no good. Especially because of iCloud’s misleading password keychain, iPhone identity theft becomes quite easy. We’ll look at this more in a moment.
Once the thieves have extracted everything of value from your device, they’ll then wipe it and resell it. The WSJ spoke with Sgt. Robert Illetschko from the Minneapolis Police Department, who said that 99% of the cases his department saw involved iPhones. This is a result of not only their popularity but their high resale value.
This video embed will take you to the exact timestamp with the quote from Sgt. Robert Illetschko, regarding 99% of smartphone thefts being iPhones.
It Goes Beyond Phone Theft: iCloud Keychain
(Not Really a Keychain.. Thanks, Apple Marketing Team)
After getting access to your phone and your PIN, thieves will use it for just about anything. To make things worse, people save so many additional log-in credentials and information on their cell phones. The iCloud Keychain is Apple’s password manager that most Apple users utilize. This saves users time and prevents them from having to enter a password each time they log onto a website or app. The passwords are stored so that users can simply log in with their Face ID, Touch ID, or iPhone passcode. Even users with two-step verification can’t prevent this one; the thief already has your device, the most likely final destination for the authentication code that’ll be sent via text or to an email/application, one that’s presumably on the device and already logged into. Once a thief has your passcode, they can access anything saved in the iCloud Keychain.
What Can They Do Now?
This is where iPhone identity theft comes into play. Thieves might use your phone to get into your bank or other financial accounts to steal or manipulate funds. As mentioned above, hundreds of thousands of dollars were stolen because of these phone robberies. An arrest warrant for a phone thief in Minnesota, for example, explains that the individual targeted bar goers and then used their phone to transfer large sums of money with bank, cash, or digital currency apps on the stolen device. When thieves can access and effectively steal your phone, they can get into any financial app on your device. This includes Venmo, Apple Pay/Wallet, Coinbase, banking apps (i.e., TD Bank, Chase, etc.), stock market apps (i.e., eTrade), and much more. It’s an enormous financial risk. Everything you’ve ever worked for — GONE (which just proves why it’s important to always keep your finances safe, even if you think they are protected digitally).
Keys to the Kingdom: iPhone Identity Theft
iPhones, and smartphones in general, are convenient but this convenience can come at a huge cost. If a thief can access your device, they can get access to your entire digital existence. Think about that for a moment. What would that look like for you? How would it affect your life personally? It’s worth reflecting on.
As easy as it seems to do so, don’t put all of your personal information – such as passwords or other login credentials – into your phone, because it can be literally stolen right out of the palm of your hands. At the very least, make this a rule when it comes to financial accounts and websites. It’s easier to rob someone who stores all of their financial information on their device. It’s much more difficult to break into someone’s house, get access to their computer and log onto their online banking.
The Risk of Our Life Being in the Palm of Our Hands: iPhone Identity Theft
When you lose your phone, the void you could be burdened with goes far beyond the loss of a materialistic item. Many of us have just about everything saved onto our tiny little devices, and this makes us susceptible to these types of targeted attacks. Thieves usually have a very good understanding of human psychology; they’re certain that the majority of us can’t resist the accessibility of smartphones, and they exploit that knowledge for profit.
It’s understandable to want to keep everything on your phone but it’s not very smart. When you save passwords in apps like Google, Safari, or iCloud Keychain, thieves then have access to these login credentials. Depending on the account, users might be prompted to put in the phone’s passcode before getting access to the account; not exactly a big ask for a thief who’s already memorized or recorded your passcode prior to stealing it. Thieves won’t just have access to the accounts on your phone, they’ll also have the freedom to act on your behalf, enabling them to move and transfer funds, or even change specific passwords should they feel so inclined, further banishing you from your own accounts.
Having Better iPhone Security to Prevent Identity Theft
Put Your Genetics Into Action With Biometric Authentication
It’s 2023; it’s time to enable biometric authentication. Biometric logins like facial recognition (Face ID for Apple users) or fingerprint recognition (Touch ID for Apple users) are a safer option for both iPhone and Android users, however, be mindful that this security measure isn’t always bulletproof. Why? It depends on the scenario. If you’re out of sight and out of reach, then sure, it’s secure but if you’re within reach but not in control, then it’s not. If you’re drugged or intoxicated, it’s easy for someone to place your finger on the phone’s fingerprint reader, and they can just as easily hold the phone to scan your face. This doesn’t make these features irrelevant or signify that they have no value but it does mean to practice vigilance, wherever you may be.

Why Androids Are Safer (in this instance)
Naturally, all of this made me wonder if an Android phone is just as vulnerable but I’m happy to report that it’s not. After entering my own passcode to access my own phone, I went to
- Settings
- Google Services
- Manage Your Google Account
- Security
- Password
And it’s not what you’d get with the iPhone experience. Google has a screen pop up that acts as a roadblock, asking you to enter your current password, along with the text, “To continue, first verify it’s you.” What a concept! This is the one password that can’t be saved, it’s the one you’re forced to remember. Otherwise, what would be the point?
Some believe that Androids are just as vulnerable as iPhones but in some cases, this has more to do with how you set up and manage your device than the device itself. Those who have been trained by employers, family members or friends on the importance of data security, probably have generally more secure devices in comparison to others.
Take the Right Steps and Prevent iPhone Identity Theft
We advise that everyone take the best measures to protect their iPhone from any compromise, especially while in public.
1. Enable Find My Phone
If you think your phone has been stolen log in to your Apple ID to find it immediately. Don’t delay, as thieves can very quickly change your password and make it impossible to find your device. (Remember the woman who reported that her Apple ID was changed within 3 minutes of the theft.)
2. Use Face ID and/or Touch ID in Public
Thieves can’t steal your biometric data as easily as they can steal your passcode. If you’re out of reach, so is their ability to access your phone. It’ll at the very least buy you some more time to try to retrieve it, do a remote sign-out or completely wipe your phone remotely.
3. Cover Your Phone
When you’re out in public, it’s best to cover your phone with your hand or body when typing in the passcode OR simply, wait to check your phone later, like when you go to the bathroom and you know you have privacy.
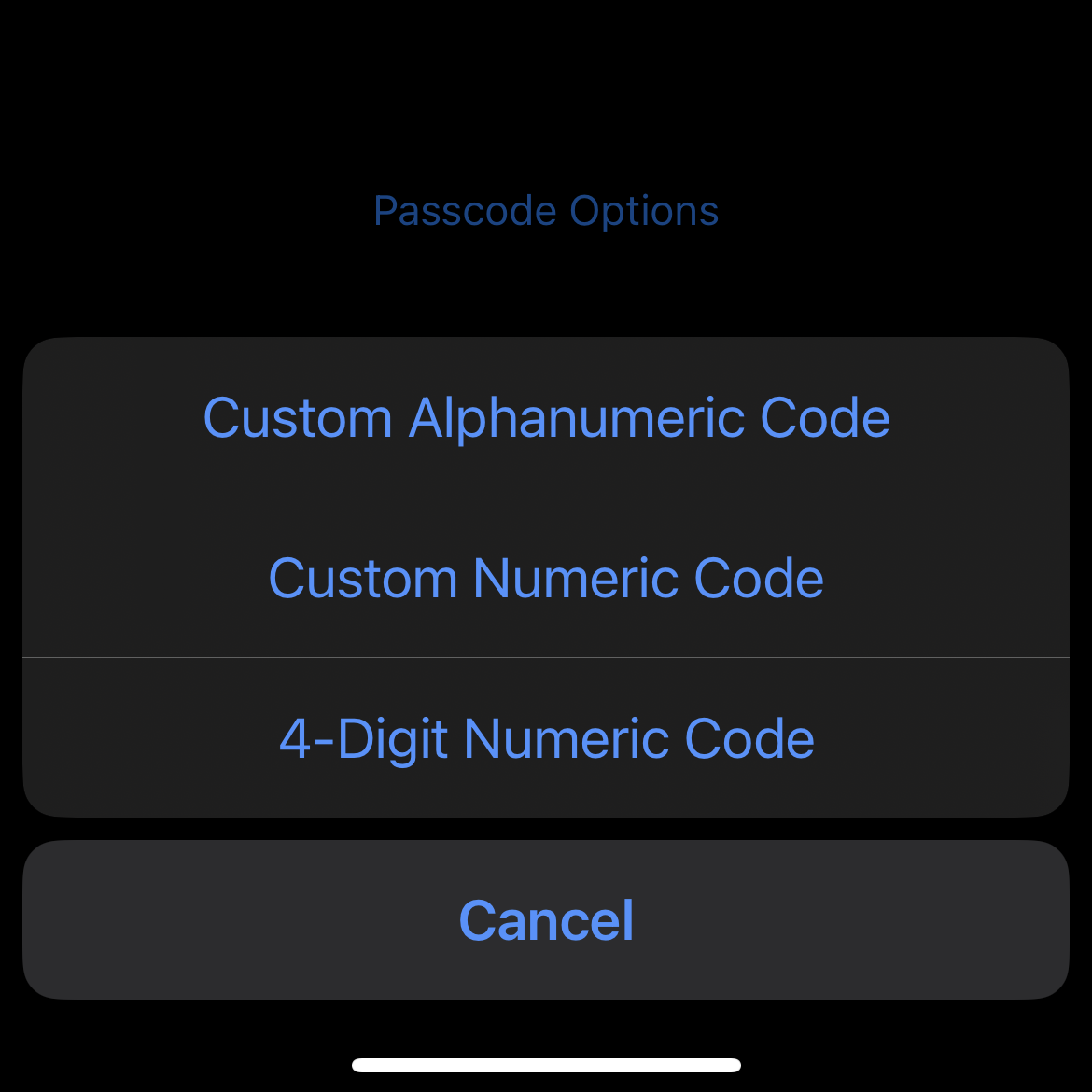
4. Forgo the Pin; Pick an Alphanumeric Password Instead
Apple has options for both 4 or 6-digit PINs and while those are incredibly convenient, they aren’t secure. To be honest, they’re probably not meant to be all that secure. Mostly, devices like these are designed to be easy but as we know, ease of use can open us up to great danger, like identity theft. Use a more secure password, like an alphanumeric one. It’ll be far more difficult for thieves to decipher your alphanumeric code in public. You can also make these more difficult to guess. Please don’t make it Password123 lol.
To change your passcode, head to the Settings app and choose “Face ID and Passcode.” It will likely prompt you to input your current passcode. From there, scroll down until you see “Change Passcode,” and by clicking “Passcode Options,” you can change your passcode to an alphanumeric password, or a 4 or 6-digit pin.
If you believe someone might have seen your password, change it immediately.
5. Don’t Save All of Your Login Credentials on the iCloud Keychain
Once an outside individual has access to your cell phone, this opens up everything that is saved. Perhaps use a separate password manager, like 1Password, that you cannot open with just the phone’s password.
6. Delete Photos of Sensitive, Confidential Documents
It’s wise to delete photos of sensitive documents, such as credit card numbers, passport information, social security numbers, financial statements, bank account information, driver’s licenses, tax documents, and so on.
To locate these photos on your iPhone, you can search through your “Photos” app at the bottom right corner of the screen. Searching the term “passport,” for example, will show any passport photos in your camera roll.

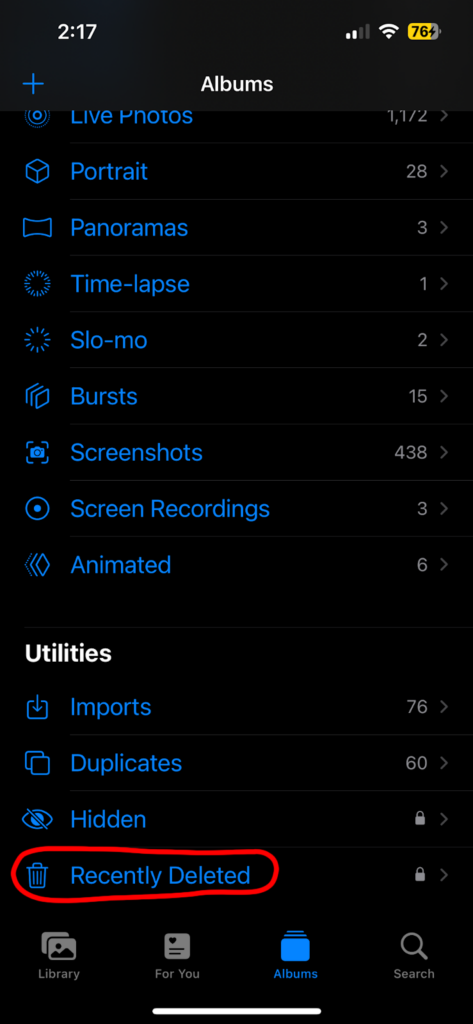
7. REMEMBER* To Delete “Recently Deleted” Photos
After deleting photos like the ones mentioned above, make sure to also remove them from the “Recently Deleted” photo album as well, which can be accessed through “Albums.”
8. MORE THAN 1 PIN
Enable passcode protection on financial apps but pick a different pin than the one you use for your phone. (Clever, clever!)
9. Utilize Apple’s “Lost Mode” Feature if Your Phone Is Lost or Stolen
Apple’s “Lost Mode” is pretty cool and it can be accessed on iCloud.com. This allows you to both lock and track your device, as well as add a custom message and contact phone number of your choice.
Apple Shortfalls
Unfortunately, many of the vulnerabilities users face with theft are due to the structure of Apple’s system. The fact that unauthorized users can easily access so many passwords and change so many settings just by having an iPhone passcode is extremely bizarre. iCloud Keychain is evidently considered to be extremely accessible for iPhone users but in unusual cases, such as these thefts, it’s not exactly convenient when stealing someone’s identity doesn’t require much effort. There should be some resistance, presented in the form of additional verification requests. Convenience should not compromise security.




0 Comments