By Mary Grlic
Phishing and pharming are the two most common types of cyber crime, making up just about 33% of cyber crime attacks in the USA (2020). In 2021, over 50 financial institutions were victims of a pharming attack against customers in the United States, Europe, and Asia-Pacific. It is no secret that phishing and pharming – two examples of “social engineering attacks” – are on the rise. With many cyber criminals trying to gain access to personal information, users must understand the risks they face in their everyday lives. An easy way for hackers to access or corrupt data is through social engineering, in which hackers trick people into downloading malware or giving sensitive information. Pharming is a type of social engineering attack that can pose enormous danger to individuals and companies. But what exactly is pharming compared vs phishing? How can you make sure you/your organization is safe from cyber attacks like pharming?
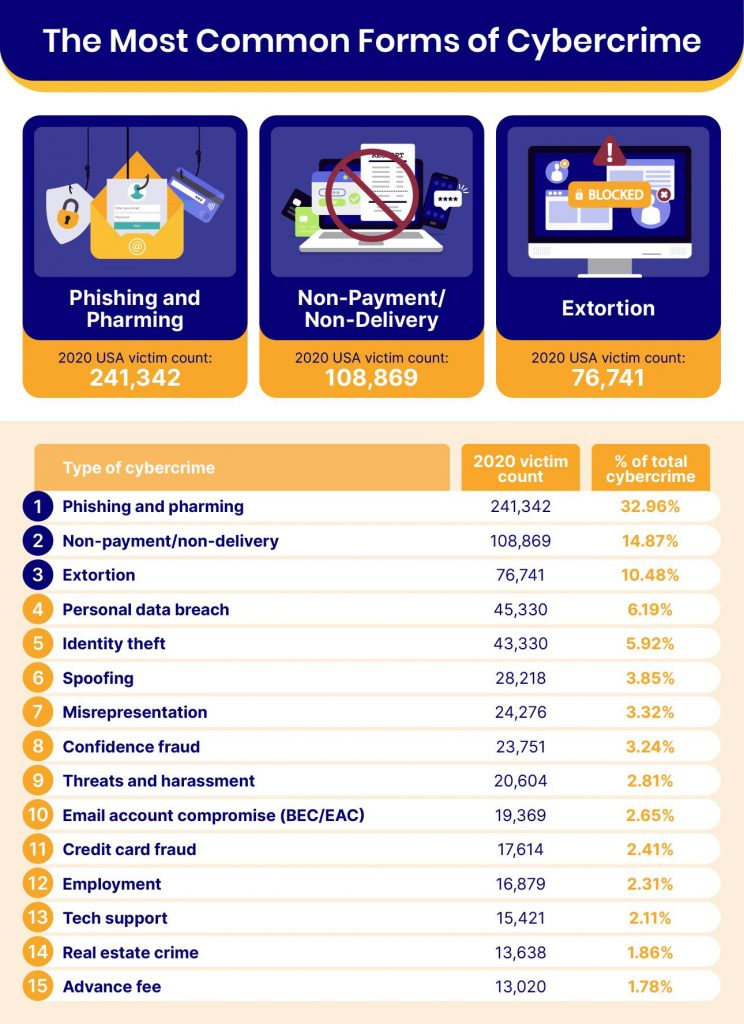
What is Pharming?
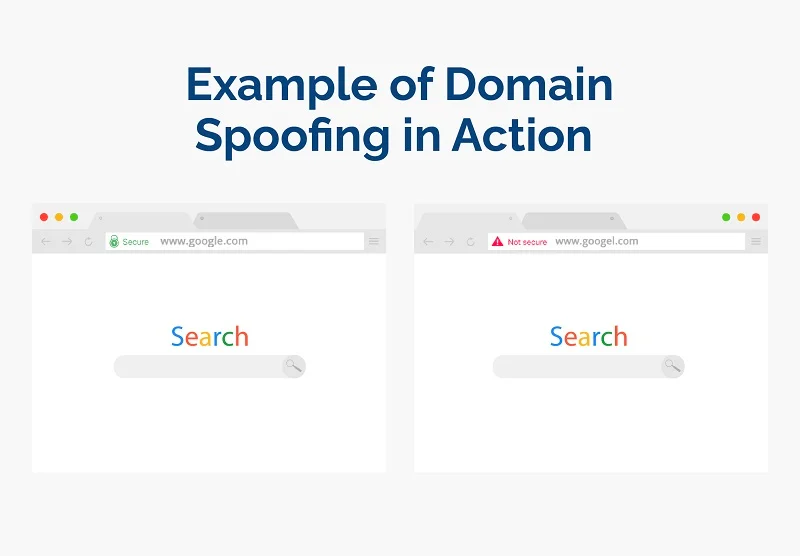
Pharming is an internet scamming process and a type of social engineering attack. Cyber criminals will redirect internet users to a “spoofed” domain. While the site will look legitimate, it is, in fact, a fake website. The site will then attempt to obtain a victim’s personal information, like passwords, social security numbers, financial records, and more. The hacker may also try to install malware onto the affected computer. The main objective of pharming is identity theft.
How does it work?
Pharming exploits internet browsing in two different ways: malware-based pharming and DNS poisoning.
Malware-Based Pharming
A hacker might send an attachment or link that contains malware in an email. The malicious code will then install the virus, which changes the computer’s hosts file to direct traffic towards a fake website. Even if you type the correct web address, you will be brought to the redirected URL. You might not even recognize that you are being brought to a fraudulent website, which is what makes pharming so dangerous. It is hard to recognize. Users might end up giving their personal data to these fake websites and putting their information at risk.
DNS Poisoning
Your domain name system (DNS) server is a protocol for how computers exchange data on the internet. Basically, when you enter a domain name into a search engine, you are trying to reach a certain IP (internet protocol) address. The DNS converts the domain into numbers, known as your IP address, so that you can access any site on the worldwide web. DNS poisoning disrupts this process. Pharmers hack the server and modify the DNS table, which causes users to visit fake websites. These fake websites can prompt users to install malware or give personal information that hackers can then steal or corrupt.
DNS poisoning is difficult because it involves attacking an organization’s network. However, these attacks can be especially harmful because it can impact multiple victims or the entire organization. It can even spread to other servers.
Pharming vs. Phishing – What’s the Difference?

Phishing and pharming might seem like similar social engineering attacks, but actually have some differences. So how do we compare pharming vs. phishing, and is one “worse” than the other? In phishing attacks, hackers essentially disguise fraudulent links or attachments so that they look reliable. Thinking it’s legitimate, a user will click on the link or attachment, only to be hacked. They might download a virus or malware, or give the attacker access to their device some other way. This type of fraud aims to gain personal information from targeted users. Phishing is evidently a huge issue for many employees and companies, especially when they do not have the proper training to identify phishing mail. Types of phishing attacks include whaling, domain spoofing, CEO fraud, and spear phishing. We have provided some tips and a detailed explanation of ideas for training employees to avoid phishing in our blog.
Pharming, on the other hand, is arguably a more advanced technique that hackers use to gain information from victims. It directs you to a site that looks legitimate, just as with phishing. Contrary to phishing, however, phishing links will prompt the user to enter login credentials in an effort to steal information. Pharming uses domain spoofing and is often more difficult to identify compared to phishing. Both are quite dangerous and have similar impacts because they’re social engineering attacks. But the way in which they attack is the main distinction between pharming vs. phishing.
Risks and Threats
Pharming attacks can be very risky for organizations and employees. The possible threats are similar when you compare pharming vs. phishing, as they are a both social engineering tactics. As mentioned above, hackers use pharming to gain access to private data or corrupt devices with malware. An attack like this can lead to a data breach in which unauthorized users get access to and steal personal information. For businesses that hold public records, such as financial information or protected health information (PHI), a data breach can be especially costly. You may risk an information leak of your client/patient information, which goes against regulations like HIPAA and will make customers lose trust in your organization. Pharming can also spread onto other devices within a network, possibly causing a virus or malware to deploy onto multiple computers. Overall, social engineering attacks like pharming are extremely harmful and pose multiple threats to any system.
Training Employees about Pharming
The unfortunate thing about pharming is that it is often hard to see. Unlike phishing, you can never really expect or know when you’re a victim of pharming. You may only be able to tell after the attack, so always be sure to look out for some signs that you might have been a victim of pharming.
- Financial transactions that you do not recognize.
- Posts or messages that you did not post, send, or type.
- Password change notifications.
- New programs on your computer that you did not install.
- You are accessing a site with an unsecure connection (HTTP vs. HTTPS).
- Site looks suspicious or the link seems illegitimate.
These indicators may be a result of pharming. You might receive a message that tells you if a password has been compromised or that someone has accessed your financial (e.x., PayPal) account – but be weary of any links in these messages! It could very well be another cyber attack (an example of phishing) with fraudulent links that could hack or attack your system. So even if it seems real, make sure these messages come from legitimate sources to best protect your network. That being said, companies often do alert you of unauthorized access to your account, like Google, which will send you a message when an unrecognized device attempts to get into your email. Just be sure not to open any links unless you are confident that you know who the sender is.
Cybersecurity Awareness Training
To best keep your business safe, provide employees with proper cybersecurity awareness training. Unfortunately, businesses are at a high risk of pharming attacks. If your employees understand how to protect their cybersecurity and how to prevent hacking, your business will be safer overall. Cybersecurity awareness training is a great way to guide your employees to identify and understand cyber risks.
Protect your Organization Against Pharming
You and your organization can take some steps to prevent pharming attacks. Make sure that all of your employees are aware of these tips to best protect your network.
- Have a reputable internet service provider (ISP). A good ISP will filter faulty or suspicious link directions by default.
- Only follow HTTPS links. TLS (transport layer security) is a network protocol that allows for safe web browsing with encryption. HTTPS is more secure than HTTP because it makes encrypted connections. HTTP links may be an example of pharming, so be sure to avoid these links unless necessary. Also, do not put any information in a site unless it is properly encrypted with HTTPS.
- Have a reliable DNS. Your DNS server is usually your ISP. You can switch to a more reliable specialized DNS service which may provide more protection against DNS poisoning.
- Avoid suspicious websites.
- Clear your browser cache.
- User a VPN (virtual private network). A VPN hides IP addresses from websites, so the entire process of pharming will be more challenging.
- Use two-step or multi-factor authentication. Hackers will need to go through an additional step to verify your identity, even if they know your login credentials. Having a strong password and verification will best protect your internet safety.
- Install and frequently update your antivirus software, along with other applications and your OS. At Computero, we use Trend Micro with our business and clients. Good antivirus softwares, like Trend Micro XDR, will protect your device from virus, malware, trojans, and more. Update your antivirus, as well as other applications and your operating system, frequently.
How Computero can Help your Business Stay Safe
Computero is a managed IT service provider that works with small and medium sized businesses in New York. We can help your business stay safe with our desktop management and server monitoring services. With good antivirus (Trend Micro), frequent OS and application updates, and 24/7 network monitoring, our technicians can help you protect your business so that you do not have to worry so much about pharming. Contact us today to learn more about our services.




